-
Our offerings
.png?width=538&height=522&name=5%201%20(1).png) SOC Services
SOC ServicesMaximize your cyber security posture.
Digital Risk ProtectionWorld-class threat intelligence to protect your organization and your customers.
ConsultingHighly specialized services to identify and remediate complex risks and threats.
Emergency Response ServicesGet a fast response from world-class experts and rapidly reinstate business continuity.
Cyber Threat IntelligenceWord-class data, analysis and insights on threat actors and the evolving threat landscape.
SPECIALIZED SERVICESWe offer specialized services to address our customers' specific requirements that have been brought about by specific market developments and trends.
- Your challenges
- Resources
-
About us
- Cyberhagen
- Careers
-
-
SOC Services
Maximize your cyber security posture.
-
Digital Risk Protection
World-class threat intelligence to protect your organization and your customers.
-
Consulting
Highly specialized services to identify and remediate complex risks and threats.
-
Emergency Response Services
Get a fast response from world-class experts and rapidly reinstate business continuity.
-
Cyber Threat Intelligence
Word-class data, analysis and insights on threat actors and the evolving threat landscape.
-
SPECIALIZED SERVICES
We offer specialized services to address our customers' specific requirements that have been brought about by specific market developments and trends.
-
-
About us
MANAGED DETECTION
& RESPONSE

We are in the
'age of resilience'
A ‘Prevent Breach’ mindset is no longer adequate.
Perimeter security has been the traditional focus to keep attackers out. But breaches can, do and will happen.
Organizations need to "Assume Breach".
This calls for a more agile, proactive and constant capability to detect and act on threats and risks already present in your network.

Most organizations
are ill-equipped
to tackle cyber challenges
- Lack of speed and scalability
- Limited access to necessary capabilities
- Complexity involved in finding the needle in the haystack
- Lack of organizational, process, technology integration
- Investigative shortcomings
Main challenges and what makes us a spectacular success
Discover the major cybersecurity challenges our customers face and learn what sets our Managed Detection and Response (MDR) service apart from an engineering perspective.
%20(1).jpg)
We are your trusted MDR services partner
Our services are delivered on top of your chosen:
Our Service levels
No matter the scope of coverage you need, we have two highly competitive service levels to offer.
.png?width=720&height=792&name=mdr_table_updated%20(1).png)
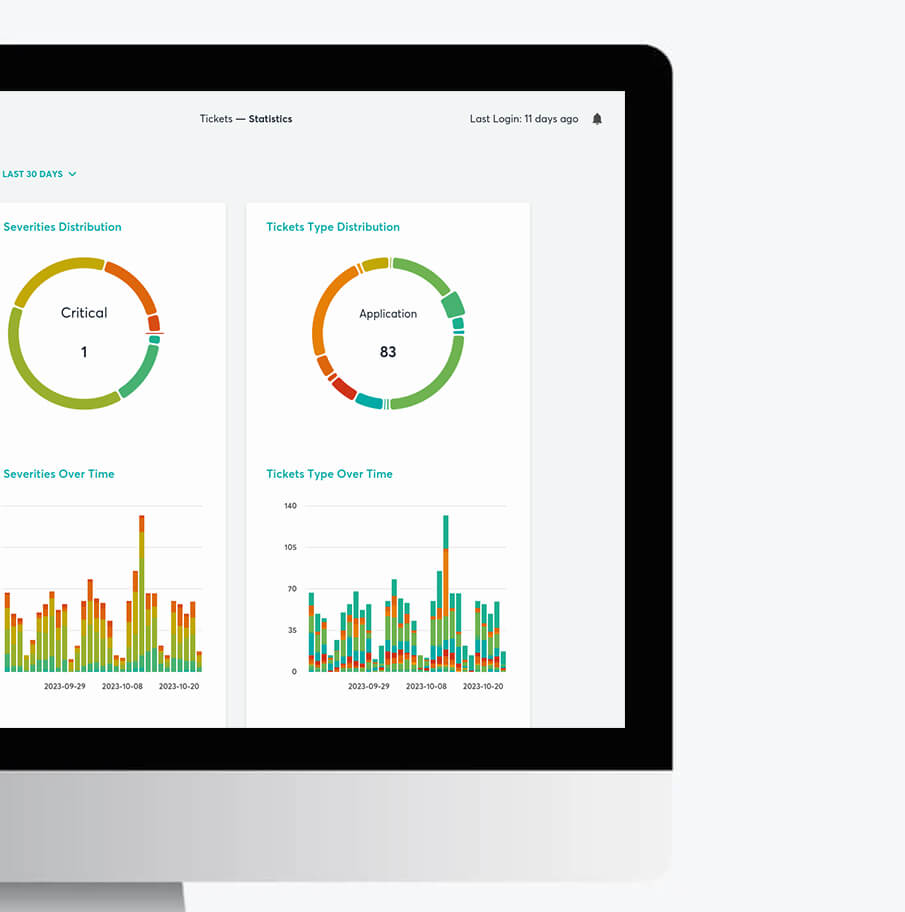
Our Threat
Intelligence Portal
Your single pane of glass. Through our TIP, you can …
Access our incident management module, which includes full audit trails on alerts and incidents
- Communicate with our team through a simple and effective ticketing system
- Manage your GDPR obligations in case of incidents
- Facilitate law enforcement notifications when needed
- Read our constantly updated security advisories (Platinum Alert Service)
- Consult our strategic assessments of threat actor and threat landscape trends (Threat Matrix)
Companies that have worked with us understand the relevance of taking out an Emergency Response Retainers with us.
Request a call
Rest Assured.
We are the leader in actionable and intelligence-driven detection and response services.
